Dish Network Still Grappling with Effects of Ransomware Attack

US television provider Dish Network is still grappling with the effects of a recent cyber-intrusion, and has so far managed only to restore a handful of services as many systems remain down.
A Dish Network representative told Mobile World Live that restoring “customer experiences” was a top priority, adding that “our teams are making progress on the customer service front every day, but it will take a little time before all of our systems are fully restored.”
Visitors to dish.com are greeted with apologetic banners directing customers to FAQs, troubleshooting guides and instructions on how to make payments, as well as a formal data breach notice last updated March 20 (as of the time of writing).
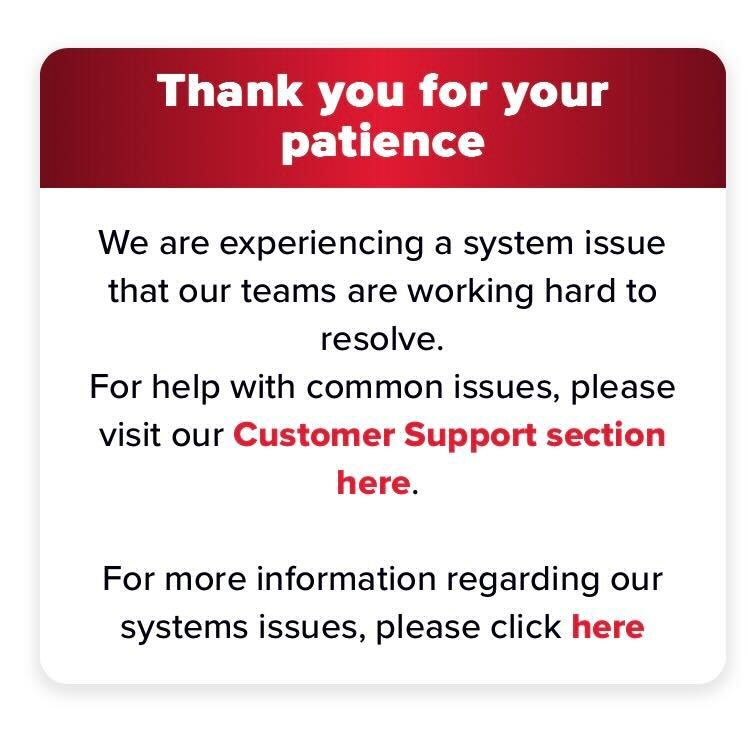
The notice includes few new details about the attack, which was disclosed weeks ago. One small uptick is that customers can go back to using a streamlined payment process for their Dish services.
“DISH customers can now make a payment through our secure payment form on our website or by mail,” the memo states.
Improvements have also been made in the customer help department, thanks to increased call center capacity, better communication on the social media front, and more care agents on hand to help with service issues.
The notice repeats the network’s original communication stating that: “It’s possible the investigation will reveal that the extracted data includes personal information.”
Dish has made no visible progress on this front so far, meaning it’s still possible that customer data was compromised in the attack. If those suspicions turn out true, “we’ll take the appropriate steps and let impacted customers know,” the broadcaster pledges.
Last week, sources close to Bleeping Computer said the Black Basta ransomware crew was behind the attack, first breaching Dish-owned Boost Mobile and then making their way onto the main Dish corporate network.
The threat actors allegedly compromised the company's Windows domain controllers and then encrypted VMware ESXi servers and backups.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
3 in 5 travel-themed spam emails are scams, Bitdefender Antispam Lab warns
August 10, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







